To make your application HIPAA-compliant, you need to implement strong security measures on both the technical and administrative sides to protect patient data and meet all HIPAA requirements.
This article will provide you with a list of specific steps you need to take to comply with HIPAA rules, backed by Seedium’s expertise in healthcare software development.
What Apps Must Be HIPAA-Compliant?
HIPAA compliance is probably the toughest part of developing healthcare applications. In its early stages, a startup can launch an MVP without full compliance, but over time, it becomes a crucial factor for growth, partnerships, and corporate sales.
However, not all health apps require HIPAA compliance. Only those that involve Protected Health Information (PHI) on behalf of a covered entity (like a hospital or clinic) or its business associates have to comply with HIPAA rules.

This applies even to modern digital tools: a smartphone app or cloud system that “touches” PHI is technically a business associate and must uphold HIPAA standards. A consumer health or wellness app used solely for personal monitoring (with no PHI transferred to a physician or insurer) typically isn’t covered by HIPAA. Some examples of applications that require HIPAA compliance include:
- Telemedicine and telehealth apps
- Electronic Health Record (EHR) and patient portal apps
- Remote patient monitoring applications
- Medical billing and insurance applications
- Condition-specific or therapy apps
- AI diagnostic or analytics software
The key question to ask to determine whether your app must be HIPAA-compliant is: “Am I working with identifiable health information presented within a healthcare context?” If the answer is yes, you must go for HIPAA-compliant app development.
HIPAA Compliant Software Development Requirements: The 5 Key Rules
HIPAA is more than a checklist. It’s a collection of regulations that target the protection of users’ healthcare data. To become compliant, you must meet requirements for physical, administrative, and technical safeguards to ensure the confidentiality, integrity, and availability of PHI.
Businesses developing HIPAA-compliant software must follow the five main rules that structure HIPAA.
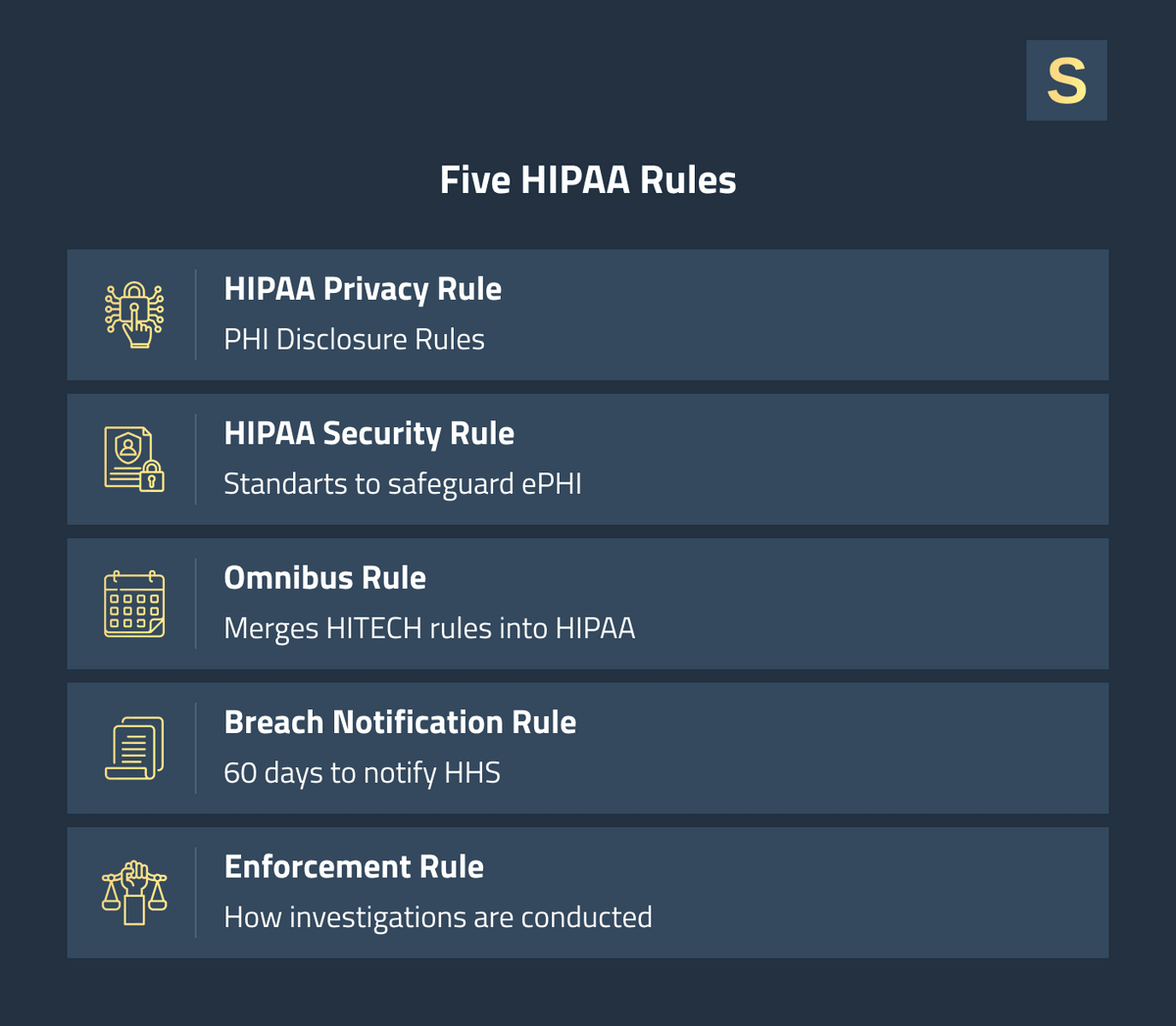
1. Privacy Rule
The HIPAA Privacy Rule establishes national regulations governing who can access or transfer PHI and under what circumstances. It defines what PHI is and provides patients with the right to manage their health information.
For example, your app must enable patients to view their data and may not release a user's personal health information to third parties except as a HIPAA exception or with the patient's consent.
2. Security Rule
While the Privacy Rule addresses what can be disclosed to whom, the HIPAA Security Rule addresses how the information is protected. On the technical side, you must use strong encryption for data in storage and in transit, authentication controls (e.g., multi-factor authentication, single logins), and maintain audit logs for access.
Physical safeguards involve securing servers and devices (e.g., locking device rooms, device management policies). Administrative safeguards include establishing proper security management procedures and an incident response policy.
The Security Rule is intentionally vague. It doesn’t say which firewall or programming language to use. Still, it makes you liable to implement "reasonable and appropriate" measures proportional to your app's vulnerabilities.
3. Breach Notification Rule
Even with robust security, incidents can still occur, and HIPAA has rules for such cases. The Breach Notification Rule requires organizations to notify relevant stakeholders when unsecured PHI is disclosed. It must be done within 60 days of the discovery of the breach.
In the case of breaches affecting over 500 individuals, you are also required to notify the U.S. Department of Health & Human Services (HHS) and the media in the impacted region. Violations of fewer than 500 records can be reported to HHS annually.
The notification steps should be incorporated into your app's breach response plan. If you have any third-party vendors (like a cloud hosting firm) that are business associates, they must inform you immediately of any incident. This ensures you can provide the required notifications without delay.
4. Omnibus Rule
The HIPAA Omnibus Rule of 2013 is generally an update that strengthened HIPAA's privacy and security provisions and expanded the reach of the law. For app developers, the most significant change was extending HIPAA compliance requirements to business associates (BAs) themselves. This means that if your company provides a service involving PHI to a clinic, you are directly liable for HIPAA compliance, not the clinic alone. The rule also requires covered entities to sign Business Associate Agreements (BAAs) with any vendor that handles PHI, outlining the vendor’s role in data protection.
The Omnibus modifications increased penalties for noncompliance, with fines reaching up to $1.5 million annually per provision, even before recent inflation adjustments. They also introduced requirements such as obtaining patient authorization to access information for specific purposes (e.g., using PHI for promotion).
If you use third-party services or vendors, ensure they are also covered under HIPAA as part of the Omnibus Rule’s scope.
5. Enforcement Rule
The Enforcement Rule grants the HHS Office for Civil Rights (OCR) the authority to investigate violations and penalize organizations that fail to safeguard PHI. It establishes a tiered system of penalties, with higher fines for greater negligence or willful misconduct.
For example, a violation involving an unresolved known security issue will be treated more severely than one resulting from an unforeseeable event. In extreme cases, criminal sanctions can be imposed. Individuals who willfully misuse PHI can face fines and imprisonment for up to 10 years for malicious breaches.
How to Build a HIPAA-Compliant Web Application
Now that we’ve outlined what HIPAA demands in theory, let’s discuss how to implement these practices when developing HIPAA-compliant applications.
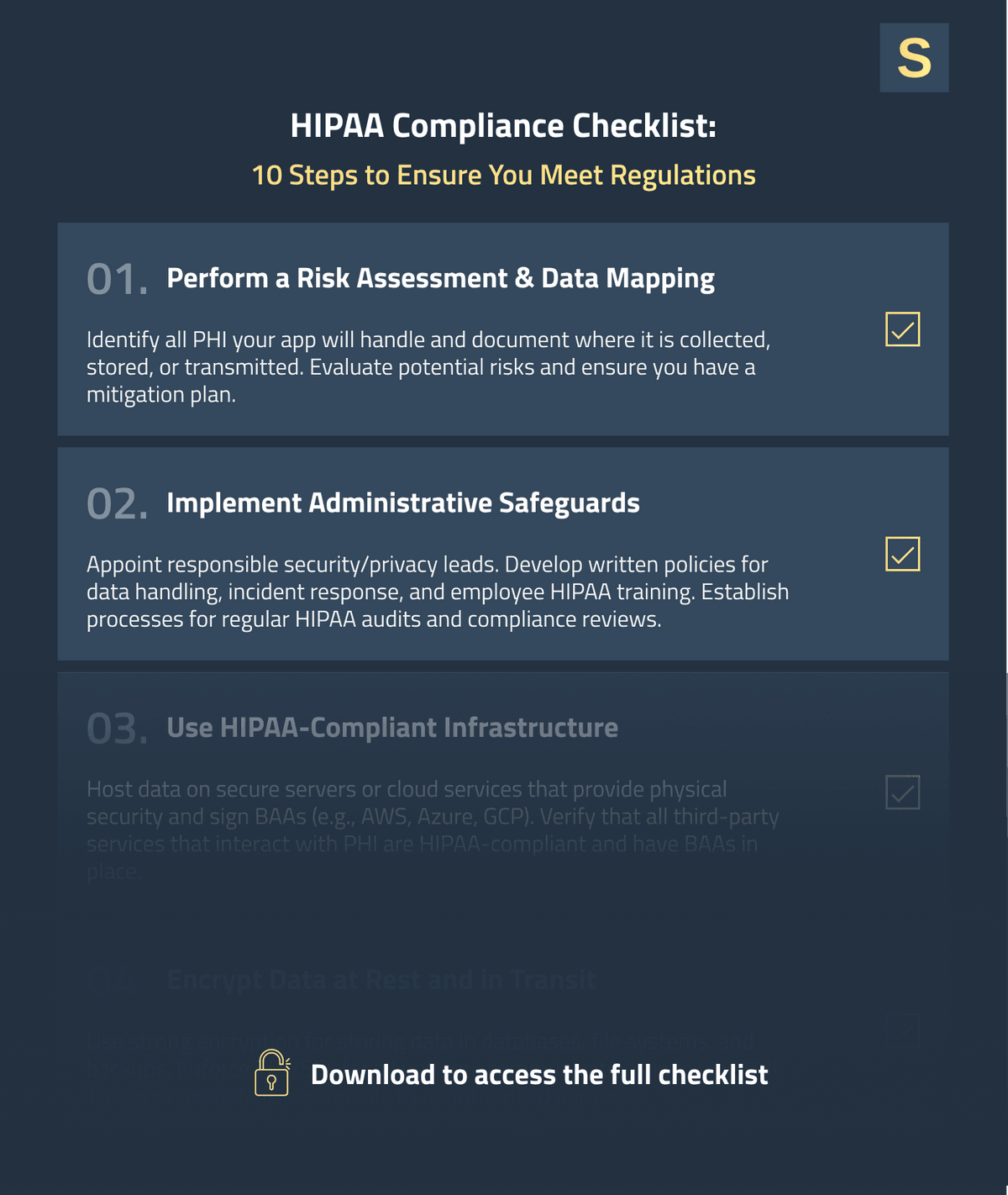
1. Start with Risk Assessment and Design Planning
Start developing a HIPAA-compliant app by defining what PHI your application will handle and mapping out data flows. Conduct a thorough risk assessment of your architecture:
- What data are you collecting?
- Where will it be stored or transmitted?
- To whom will it need to be made available?
This will identify potential vulnerabilities from the beginning. You must plan your system architecture keeping HIPAA in mind: segregate databases so that PHI is kept away from other data, and define built-in security measures upfront (encryption, auditing, etc.).
2. Implement Strong Data Encryption (at Rest and in Transit)
Encryption is your first line of defense in protecting PHI. You should encrypt all sensitive information, both in transit and at rest.
Most modern databases and cloud storage solutions have encryption integrated, so you just need to turn it on and safely store your keys. For PHI "in transit" (moving across networks), deploy TLS/SSL encryption on any connection that handles PHI.
3. Secure User Authentication and Access Controls
PHI access must be strictly controlled. Your application should have strong Identity and Access Management (IAM) policies so that only authorized users can access sensitive data, and only the minimal data necessary for their role. To achieve this:
- Start with strong authentication for each individual user account: require strong passwords and consider setting up multi-factor authentication (MFA) for any user who will view PHI (doctor, patient, or admin).
- Role-Based Access Control (RBAC) is a widespread technique in access control. Determine the roles your system needs and apply each role with only the needed privileges. For example, a patient can view only their records, and physicians can view the records of their patients.
- Implement session timeouts and secure account recovery practices to prevent unauthorized use of stale sessions or compromised credentials.
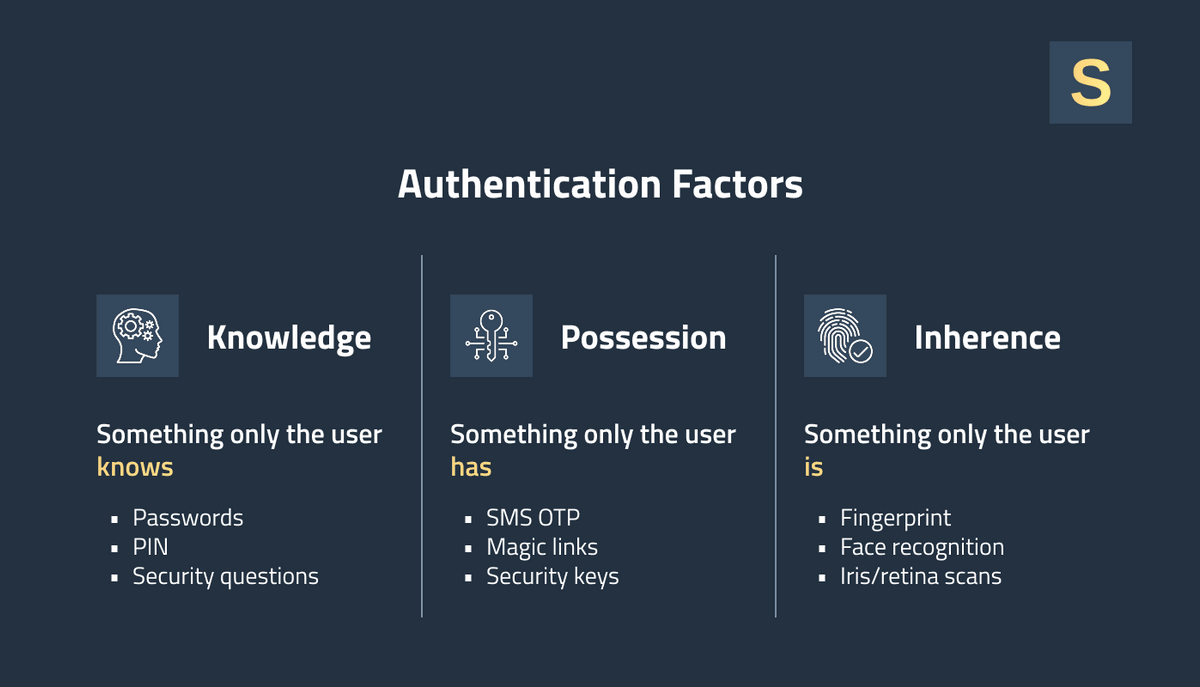
New authentication platforms (Auth0, Okta, Firebase, etc.) can make this easier to implement, and some offer HIPAA-compliant features (assuming you sign a BAA). By controlling who can log in and view data, you meet a large portion of the Security Rule mandates and significantly reduce the likelihood of a breach.
4. Maintain Audit Trails and Monitoring
HIPAA requires you to have access to auditing capabilities for PHI. Include logging and monitoring in your app from the very beginning. Each time PHI is viewed, created, updated, or deleted, your system should log who performed the action, what was done, and when it occurred.
For example, if an admin views a patient's lab report or a doctor alters a note, record the user ID, timestamp, and activity. These logs must be stored securely, so use write-once databases or third-party logging services with append-only entries.
In addition to logs, enable real-time monitoring and alerting for suspicious behavior. Anomalies like an unusual querying pattern of user accounts grabbing thousands of records within a matter of minutes, or attempted failed logins, should trigger alerts to your security team. Many tools can help in flagging anomalies, from SIEM solutions to simple CloudWatch services.
5. Backup Safety and Data Integrity
Protecting data integrity is just as important as securing access to it. For instance, your system might hash every medical record or leverage database features like row-level encryption and integrity validation. If anything seems fishy (e.g., a hash no longer balances against the data), you can mark it.
Backups must be run routinely so patient information isn't lost forever due to a system crash or ransomware attack. At the same time, backups themselves must be encrypted and stored securely. Remember, a backup is essentially another copy of PHI that needs protection just like the primary data store.
Check out the case study of healthcare analytics platform development.
6. Plan for Safe Disposal of Data
This involves defining how long you'll keep various kinds of data and how to securely delete it when the time comes. For example, you might decide to erase some health records or user accounts after X years of no activity unless regulation requires holding on for longer. When erasing data, make sure that it can’t be recovered. Technically, employ techniques like cryptographic erasure for disk data or securely overwriting.
For even ordinary processes such as getting rid of error log files or outdated backups, check to see if they have PHI and deal with them appropriately. The most frequent trap is remembering that PHI may reside in the most unlikely places, such as logs, temporary files, cache, etc. Set up a time-based schedule to get rid of these, too.
7. Document Policies, Train Staff, and Remain Up-to-Date
You also need strong administrative processes and training in place. Document all of your security and privacy policies. For example, how access is assigned, how incidents get addressed, and developer guidelines for coding securely.
Make sure you have a Privacy Officer and a Security Officer on your staff to monitor ongoing compliance. Hold regular training sessions so everyone working on the HIPAA compliance software development is aware of HIPAA responsibilities.
Software developers should be trained on topics like not hard-coding PHI or secrets, avoiding insecure coding practices, and how to handle code that deals with health data. Operations staff should be trained on how to respond if a potential breach occurs.
HIPAA-Compliant Software Development Examples
We provided our healthcare software development services to launch more than 200+ products, a significant part of which are related to the healthcare sector. Since most of them fall under the NDA, we’ll share anonymized examples of HIPAA-compliant software development to illustrate how it can look in practice.
Case Study #1: Ensuring HIPAA-Compliance for a Medical CRM System
Client: A US-based healthcare provider that needed a web-based CRM for managing patient relationships and appointment scheduling.
Project goal: Ensure strict HIPAA compliance for all PHI accessed or displayed in the browser.
Core solutions to ensure HIPAA compliance:
- Role-based UI & data access: Our engineers built dynamic dashboards where visible fields and actions adapt to the user’s role (doctor, nurse, billing, admin). We also used front-end authorization checks in addition to back-end enforcement to prevent accidental PHI exposure.
- Secure session & authentication: To ensure a reliable identity check, we implemented multi-factor authentication. Sessions auto-expire after inactivity with a grace period warning modal before logout.
- PHI handling in the browser: We ensured PHI isn’t stored in browser storage and implemented in-memory data rendering that clears all PHI when a session ends or a tab closes.
Outcomes: The solutions implemented by the Seedium team on the front end strengthened the client’s back-end security mechanisms and enabled them to achieve full HIPAA compliance.
Case Study #2: Expanding Functionality of a Fitness Application
Client: A fitness app company expanding its functionality to let patients share exercise and recovery progress with their doctors.
Project goals: Enable secure sharing of health metrics between patients and providers, meeting HIPAA requirements.
Core solutions to ensure HIPAA compliance:
- Role-based access control: We built role-based dashboards that dynamically adjust visible components depending on the user role, ensuring that no unauthorized data is rendered in the UI.
- Privacy-focused UI features: All front-end forms and API calls were designed to send or display the minimum necessary data. We also added an automatic screen lock after inactivity to prevent accidental exposure in public settings.
- Front-end data protection: Our engineers ensured PHI is never stored in browser localStorage, sessionStorage, or mobile app persistent storage. We used in-memory state management, so sensitive data only exists during the active session.
Outcomes: Our work enabled the client to successfully pass the HIPAA compliance audit for front-end PHI handling and positioned them to progress toward full compliance.
Develop HIPAA-compliant Software with Seedium
Seedium has been helping healthcare providers build and scale software products for over 8 years. We understand how important HIPAA compliance is for your business success and have practical experience in applying best security practices to help you meet all the requirements on the tech side.
Our tech leaders can assist you in implementing strong security features like encryption, access control, and audit logging as core elements rather than afterthoughts. Whether you already have a product in the pipeline or are just planning development, we can quickly step in to help you move forward faster and with more confidence.
Feel free to contact us to discuss your needs and how we can meet them with our healthcare software development services.
HIPAA Compliance Checklist for Software Development
As a quick reference, we’ve distilled the above recommendations into a HIPAA compliance software checklist you can use throughout your healthcare app development process. Feel free to download it below.