Access control is the set of rules and mechanisms that decide who can do what to which data in your SaaS product.
What are the types of access control?
In practice, you’ll see a few models of access control:
- RBAC (role-based) assigns permissions through roles like Admin, Manager, or Viewer and is the most common in B2B SaaS.
- ABAC (attribute-based) adds attributes to users, such as department, region, client level, time of day, etc., based on which the system grants or denies access to resources.
- ReBAC (relationship-based) is founded on graph relationships between users and resources, such as owner, editor, or viewer, and is appropriate for collaboration or sharing-heavy apps.
- DAC (discretionary) lets resource owners allocate access, which is typical for document sharing.
- MAC (mandatory) is based on strictly defined rules, backed by security policies, and prohibits individual resource owners from granting or denying access to resource objects.
Most teams today externalize rules with a policy engine (typically an ABAC/ReBAC hybrid) so that policies are testable and versioned rather than hard-coded.
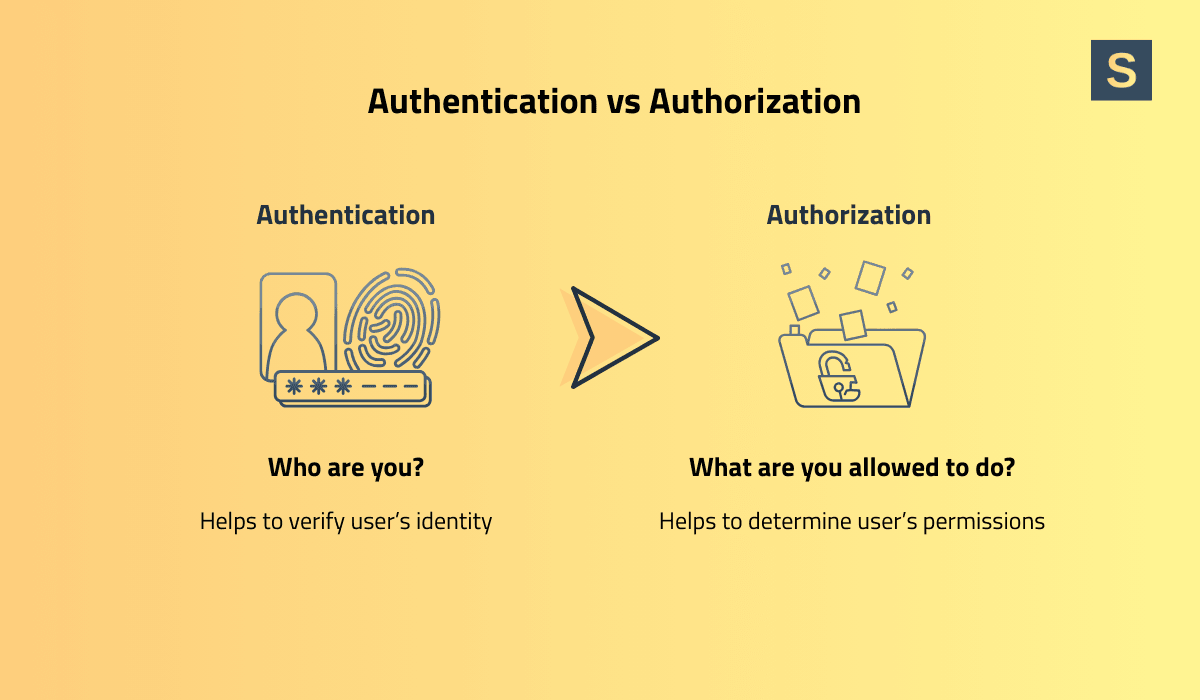
What is the difference between authorization and authentication?
Authentication confirms identity ("Are you Alice?") via logins, tokens, or SSO. Authorization confirms permissions ("Is Alice permitted to modify invoice #123?"). Authentication precedes. Then, Authorization uses the authenticated identity, resource, and context to make a decision.
How do you implement access control in SaaS?
To implement access control in your SaaS product development, you should follow the next steps:
Choose an access control model
Start with RBAC for simplicity, add ABAC conditions as needs arise (region, record owner, plan level). If centered on teams/projects or sharing is your core UX, adopt ReBAC from the outset.
Design permissions and roles
Inventory your resources (workspaces, projects, records) and user actions (read, create, update, delete, export, invite). Then, map them to a small set of default roles with room for fine-grained permissions and enterprise tenant custom roles.
Complete authentication first
Ensure identities are trustworthy before enforcing permissions. Ensure secure authentication by using
- OAuth2/OpenID Connect (e.g., Auth0, Okta, Firebase Auth) for standards-based SSO and token issuance.
- Two-Factor Authentication (2FA) (TOTP, WebAuthn/passkeys, SMS as fallback) for higher assurance.
- JWT or session-based authentication:
- * JWTs: stateless, include claims (sub, roles, tenant, scopes); short expirations; rotate signing keys; validate audience/issuer.
- Sessions: server-side, rotate session IDs, secure/HttpOnly cookies, CSRF protection for browser apps.
Make tokens short-lived and refresh them securely, regardless of the method you use.
Handle multi-tenancy access
Multi-tenant apps must aggressively isolate data. Key solutions here:
- Include a tenant ID in user claims, resources, and all queries.
- Scope every query by tenant.
- Provide audited, time-boxed “break-glass” procedures for cross-tenant support tasks.
Make it auditable
Serve as a ledger for access:
- Log access control decisions: actor, action, resource, outcome, tenant, reason/policy ID, timestamp, request ID.
- Track role/permission lifecycle: who granted/revoked what, when, and for which tenant.
- Audit trails for sensitive actions: exports, deletes, and billing changes.
- Surface reports: periodic access reviews for admins; alerts for anomalous access patterns.
Test and review
Write positive and negative tests for every action and role, along with multi-tenant isolation tests that attempt to access cross-tenant access. When employing a policy engine, keep policies in version control with unit tests based on actual scenarios.
Conduct security testing for frequent failure modes like IDOR (insecure direct object references) and compromised object-level authorization. From an operational standpoint, audit least-privilege regularly, delete inactive admins, rotate tokens and keys, and run incident runbooks.
Check out more SaaS terms in our SaaS glossary for business leaders.
Build and scale your software products with Seedium
Seedium is a trusted web & mobile development company that helps businesses build and scale their software solutions. Since 2017, we have successfully launched over 200 products in more than 15 industries, including SaaS, HRTech, and HealthTech.
Seedium offers a wide range of design & development services to help you achieve your business goals efficiently:
- Web & mobile application development;
- UX/UI & product design;
- Custom software development & integrations;
- AI development;
- Scaling product architecture;
- Providing dedicated development teams.
Feel free to contact us to start a conversation about your project. Let’s build something great together!