Mobile Application Security is a constant concern for many enterprises. However, to build a solid reputation and gain consumer trust in your brand, the security of your web product should be a top priority. The number of cyber attacks is increasing every day, and if you do not protect your mobile application properly, there is a risk of leaking confidential and vital information.
To help you avoid this, we've provided a comprehensive and detailed checklist of ways to ensure maximum security for your mobile app and reduce the likelihood of external cyber threats getting into your app.
The Importance of Mobile Application Security
The world is becoming more dynamic every day, and companies are trying to make their online product available from any mobile device. This leads to the fact that consumers increasingly share their personal information in the mobile app or mobile website. In addition, most applications are connected to the cloud and work across multiple networks. It makes mobile apps vulnerable to security threats and cyber-attacks.
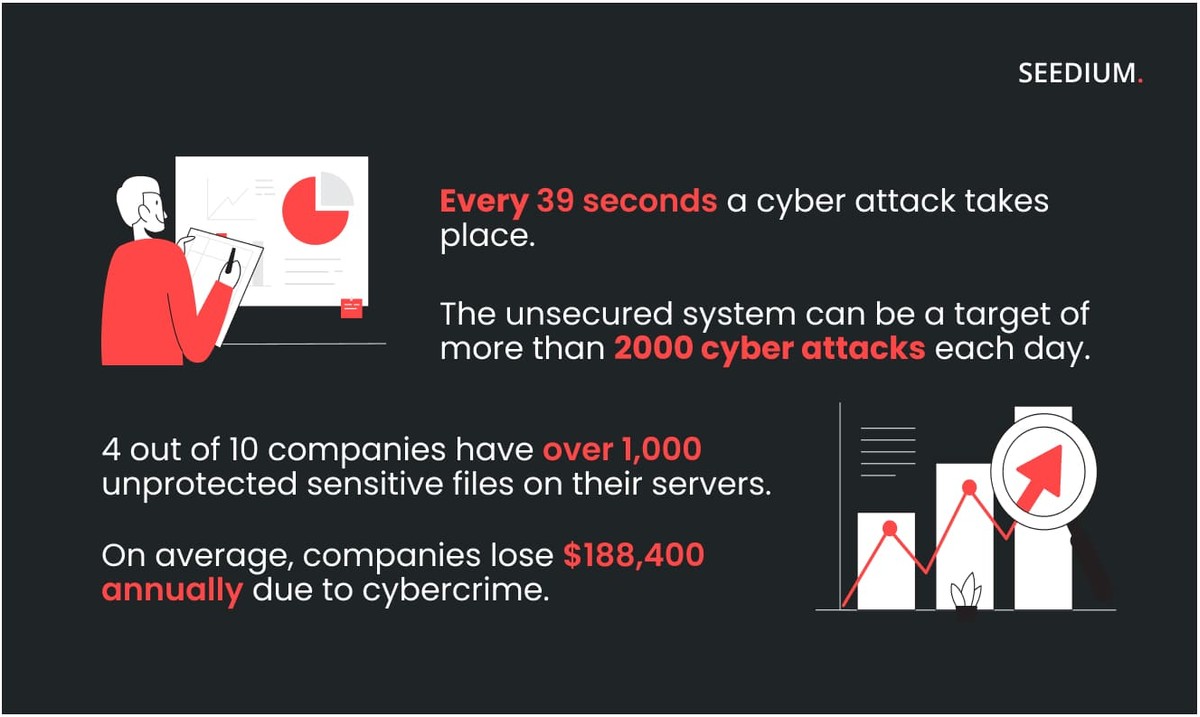
Source: Cybersecurity statistics
Timely security measures can prevent this and ensure that application data are protected from potential danger.
Mobile application security is the process of testing and preventing potential attacks on mobile application data. These measures include solutions aimed at protecting the application not only during the development process but also after its deployment. In other words, application security is a comprehensive concept that includes processes, tools, and techniques to protect applications from threats throughout their lifecycle.
Implementing effective application security is a worthwhile investment and is essential to business success. It improves app efficiency, reduces risk, and enhances trust between businesses and users. In summary, mobile app security helps to:
- reduce the risks of user data leakage;
- prevent a potential break-in;
- reduce the likelihood of negative consequences from hacking;
- preserve the company's reputation and client base.
The Common Mobile App Security Threats
Cybercriminals are well-organized and highly specialized and motivated enough to discover and exploit vulnerabilities in corporate applications and steal data, intellectual property, and confidential information. Application security solutions can protect any application used by internal customers, business partners, and employees.
In practice, compliance with information security is a timely response to possible shortcomings. On average, there can be more than 30 vulnerabilities per application, six of which are critical. The most dangerous consequence of vulnerabilities is data leakage.
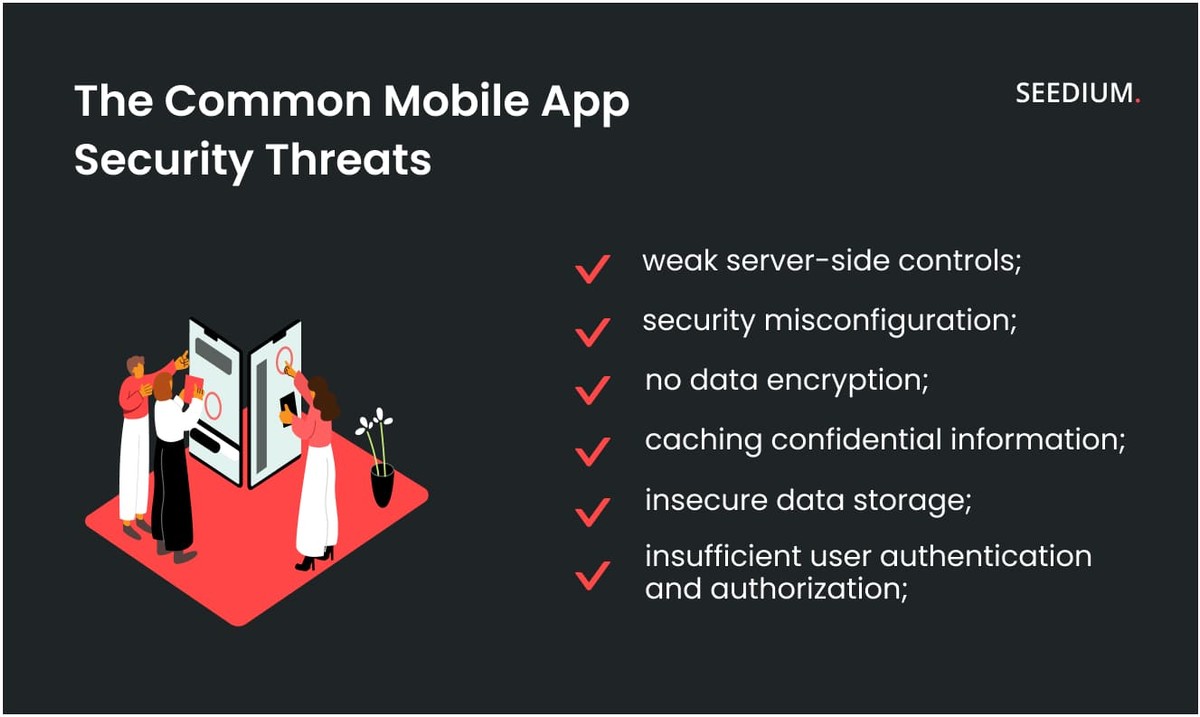
Its reasons usually lie in the lack of administration and access control to various devices. Sensitive data should not be kept in the public domain. Strong cryptographic algorithms should be used to protect them.
Lack of mandatory authentication and incorrect session management can also contribute to the theft of confidential information. To avoid this, you need to use exclusively multi-factor authentication, check user sessions, and store authorization tokens in the most secure areas of the OS. Safe and correct work with data is especially important when it comes to applications that use a large amount of personal information.
Another serious vulnerability is insecure communication, which is characterized by insufficient authentication of communication origins, incorrect SSL versions, and incomplete negotiation checks. The use of certificates will ensure a secure exchange of data transfer only in encrypted form
One more secure threat is related to the fact that most mobile applications require offline use. At the same time, authorization with data storage is used: after entering the login and password, the program saves a special identifier for further presentation on the server. The vulnerability of authorization methods can provide access to sensitive information or application functions, so you need to take care of the correct distribution of access rights.
In addition, quite often hidden functionality is present in the application code: information for testers, "invisible" settings, and even some keys. It is necessary to carefully check device identifiers and open access to hidden sections only on the devices of developers or testers.
To detect all these potential risks in time and ensure information security, it is necessary to regularly test applications.
Mobile Application Security Testing

Application testing covers discovering data security issues, session management, authentication, and authorization. For better results, create a list of common threats and security issues. Don't forget to cover each OS version and phone model. This gives a clearer picture and makes the next steps easier and more efficient.
The checklist depends on the nature of the application and the industry you are developing it for. Here are some common weaknesses to include in your testing checklist:
- Point of entry;
- Data transfer;
- Data store;
- Data leak;
- Authentication;
- Server Side Controls.
There are also many security testing tools available to help analyze the security of your mobile app, so you can choose the one that best suits your project's testing requirements. For example, Perfecto is one of the best mobile and web testing tools in the cloud, as well ACCELQ is the optimal option for the codeless test.
Steps to Improve Mobile Application Security
In general, mobile application security consists of the protection of three components: the client part, the server part, and the communication channel. Let's look at the key solutions to prevent the most common security issues and make your app safe.
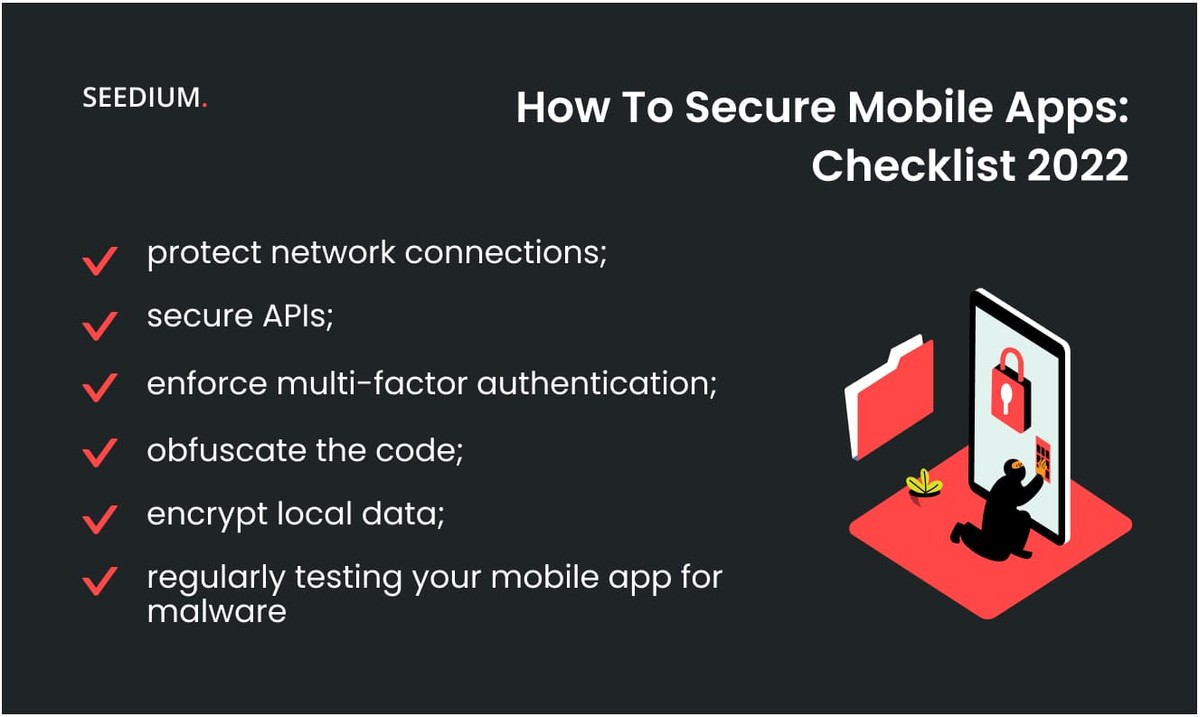
1. Secure APIs
Mobile applications can communicate with each other through an Application Programming Interface (API). APIs are vulnerable to hacker attacks, so protecting them becomes a necessity. Things to avoid such possibilities include using authorized APIs in the application code.
A common way to create a secure and trusted API is to use API keys. The bonus of using them is that you get built-in analytics, as the API key helps to track usage metrics.
2. Protect network connections
When it comes to mobile app security, network connections cannot be ignored. To avoid unauthorized access, cloud servers and servers accessed by APIs must be secured.
Often the developers use the containerization approach which involves linking an application with its libraries, dependencies, and configuration files to run error-free across multiple computing environments. This solution helps securely store every document and data in an encrypted container. While there are many containerization ecosystems, Docker and Kubernetes dominate.
To add additional layers of security, it is advisable to encrypt the database using SSL (Secure Sockets Layer), TLS (Transport Layer Security (TLS), or VPN (Virtual Private Network).
3. Encrypt local data
Attackers often take advantage of data stored in applications on mobile devices. This is why encryption of locally stored data becomes a necessity.
Applications must be developed with user data privacy in mind. Make sure that credit card details and passwords are not stored directly on the device. If the app requires you to store them on your device, ensure you do so encrypted.
4. Obfuscate your code
This strategy is used to confuse hackers by making machine code or source code difficult to understand. Various obfuscation tools are available on the market such as Obfuscator.io, or PyArmor.
This can also be done manually by removing non-essential metadata and debugging information. As a result, the information available to an attacker is significantly reduced. It also improves runtime performance in most cases.
5. Enforce Strong Authentication
To prevent unauthorized access and password-guessing attacks, you should implement multi-factor authentication. For example, a password or PIN in combination with confirmation on the device. As for validation, set a limit on the minimum password length, and also check for a match with the login, e-mail, and site address.
6. Check incoming data
Control the data received from web forms, both on the client side and the server side. The browser checks for simple errors like an empty required field or text entered in a numeric field. These checks are bypassed, so server-side monitoring is required. Lack of server-side validation leads to attacker exploitation of injections and other types of attacks.
7. Use updated libraries
Libraries are one of the common elements that are subject to attacks. The risk is directly proportional to the length of your code. When working with a mobile application, use only the latest versions of libraries with all available improvements and changes to avoid security breaches.
Securing Mobile Applications: Seedium’s Approach
It is very important to apply a holistic approach to web product security at all stages of the project, from design and development to deployment, and at all levels of the information system: in the network, on the server, and in the application itself. Therefore, at Seedium we observe the safety of our projects with special responsibility, and monitor compliance with all security requirements:
- we use only proven technologies and working solutions;
- our specialists carefully develop reliable and secure web product architecture;
- we identify potential application vulnerabilities and ways to prevent them;
- Seedium team conducts in-depth testing and eliminates the identified problems;
- actively use security-oriented programming techniques.
This approach helps us comprehensively prevent the possibility of compromising the integrity, availability, and confidentiality of information technology products, services, or infrastructure.
Final Thoughts
Any compromise on integrity, authentication, and availability renders the software insecure. To understand how to ensure the security of the application, you should study the most dangerous vulnerabilities, take them into account at the development and testing stages, and if they are identified, eliminate them and be sure to document all the problems found in order to avoid them in the future.
If you apply all the strategies discussed above, it will be hard for a hacker to break into your application. Moreover, most of the methods described above are easy to implement. However, it's equally important to stay up-to-date with the latest cybersecurity tools and techniques to further protect your application. Likewise, monitor abuse by attackers for data breaches and threats. Also, you can always use our mobile application development services to achieve the best results.